Overview
In this post, I will provide the step by step guidance for integrating Azure Active Directory with VMware Workspace One Access as a 3rd party identity provider (IDP) and enabling true single sign on (True SSO) feature on Horizon Cloud Services (HCS) on Azure to allow the users to access desktops/apps without prompting for password.
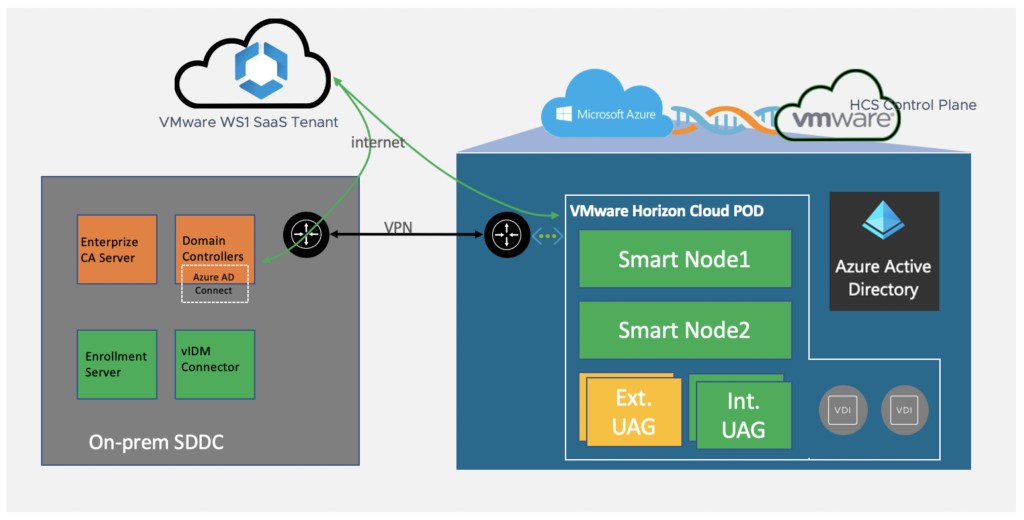
My environment looks like below.
Requirements
- Microsoft Azure Active Directory instance.
- VMware Workspace ONE Access tenant (SaaS or On-prem) integrated with HCS on Azure POD. Refer to docs.vmware.com
- True SSO feature enabled VMware HCS on Azure POD. Refer to docs.vmware.com
- Login to your Microsoft Azure portal (https://portal.azure.com) > [Home] > [Azure Active Directory].
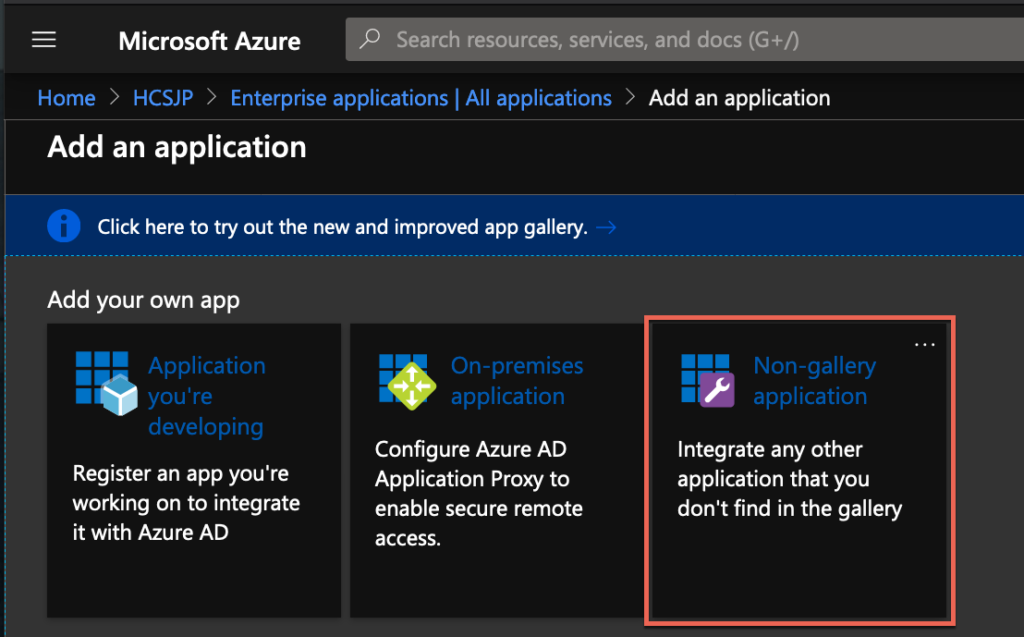
2. Select [Enterprise Applications] > [New Application]
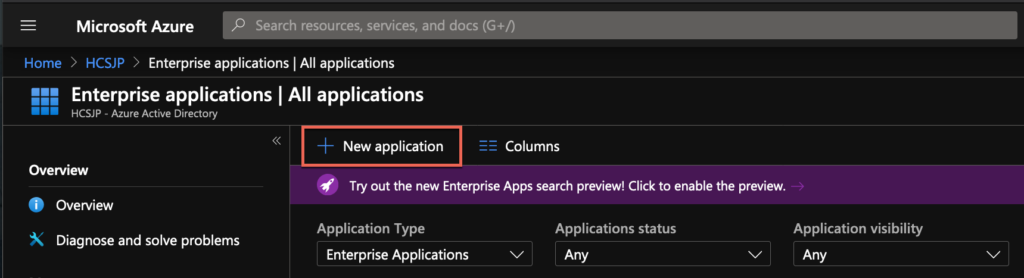
3. Select [Non-gallery application] and give a unique name to the application. In my case, I am naming as [HorizonCloudOnAzure] and select [Add].
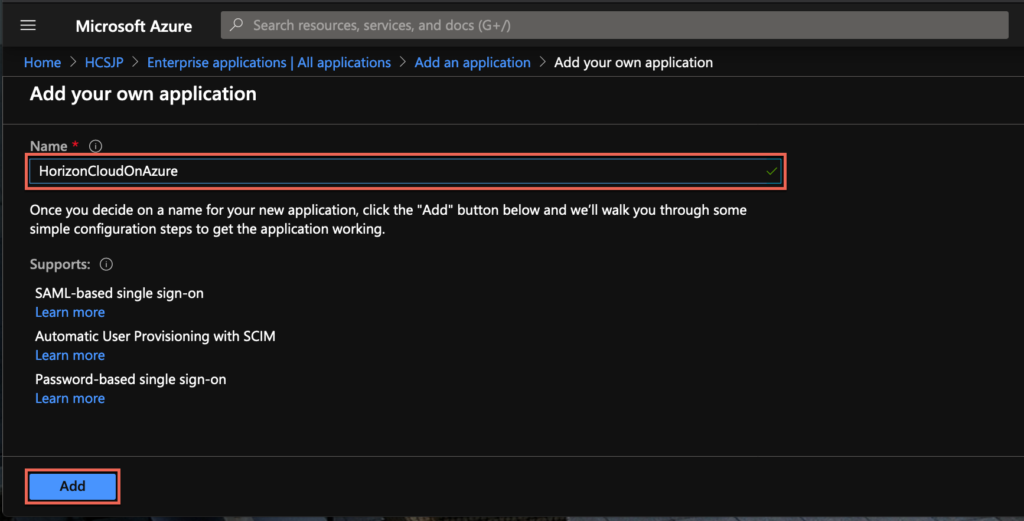
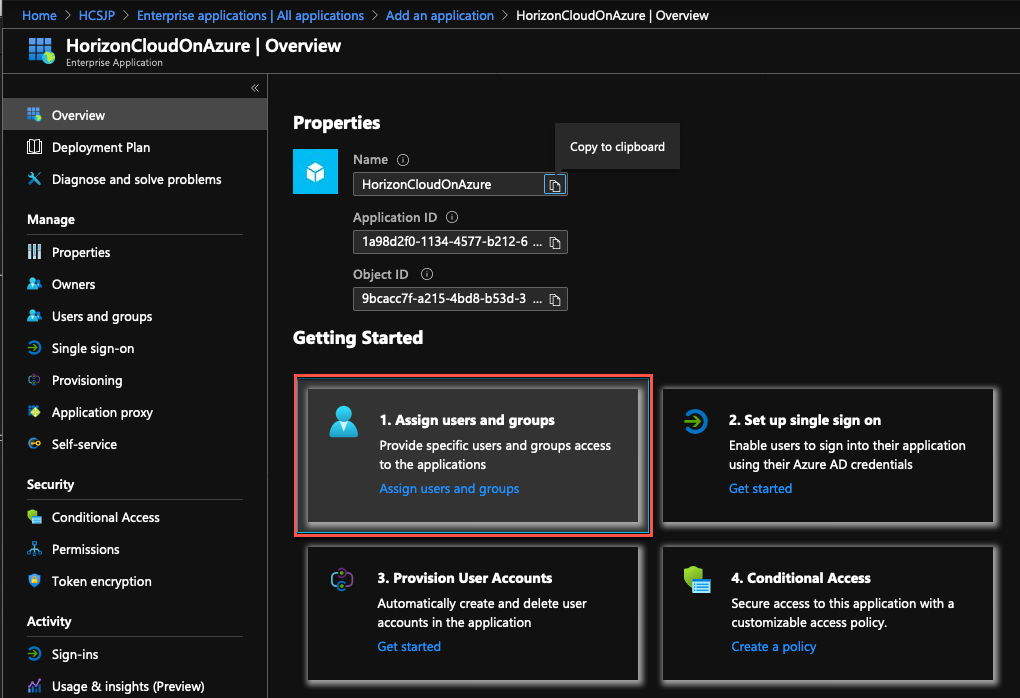
4. Confirm your application has been created, then select [Set up single sing on] under Getting Started .
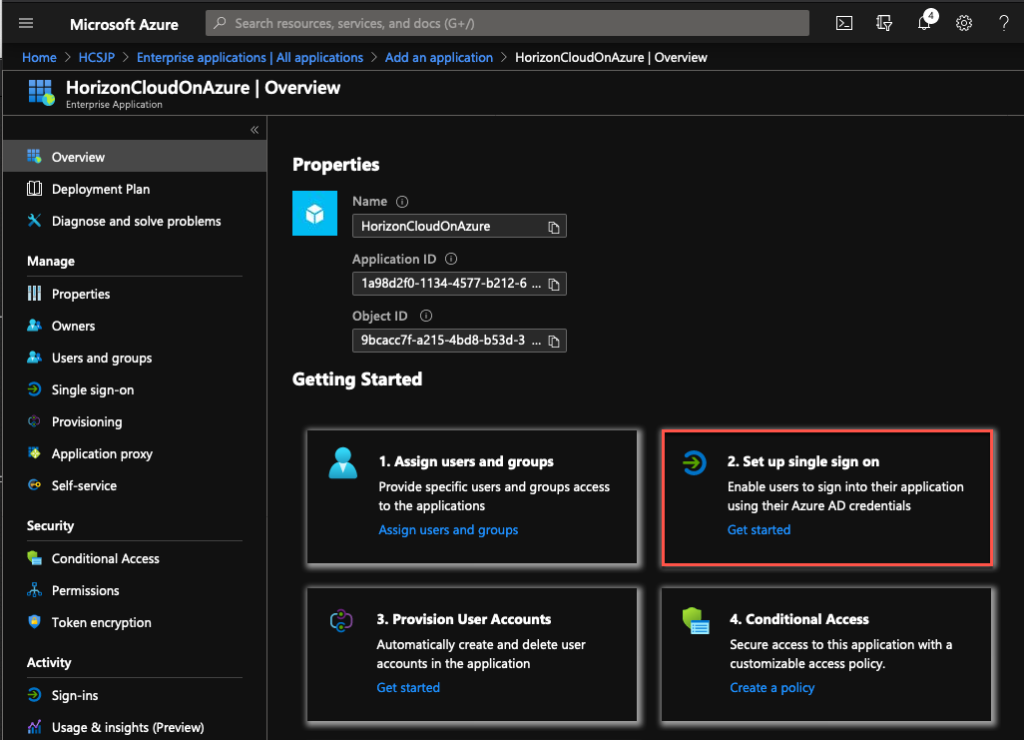
5. Select [SAML] under single sing-on method.
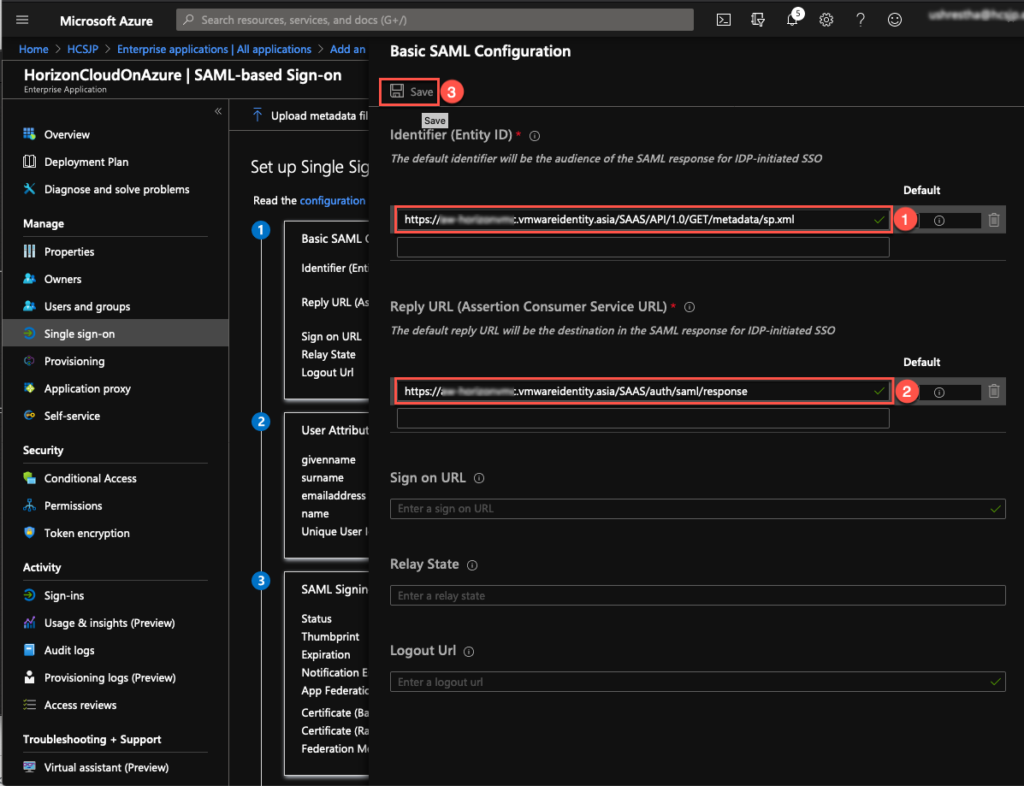
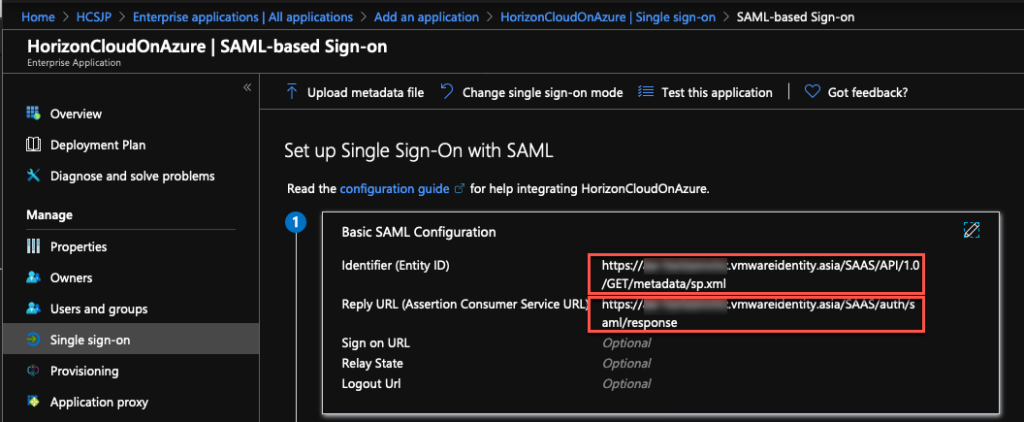
6. Click on [pencil icon] next to [Basic SAML Configuration] and configure [Identifier] & [Reply URL] as per the information in below xml and [Save] the configuration.
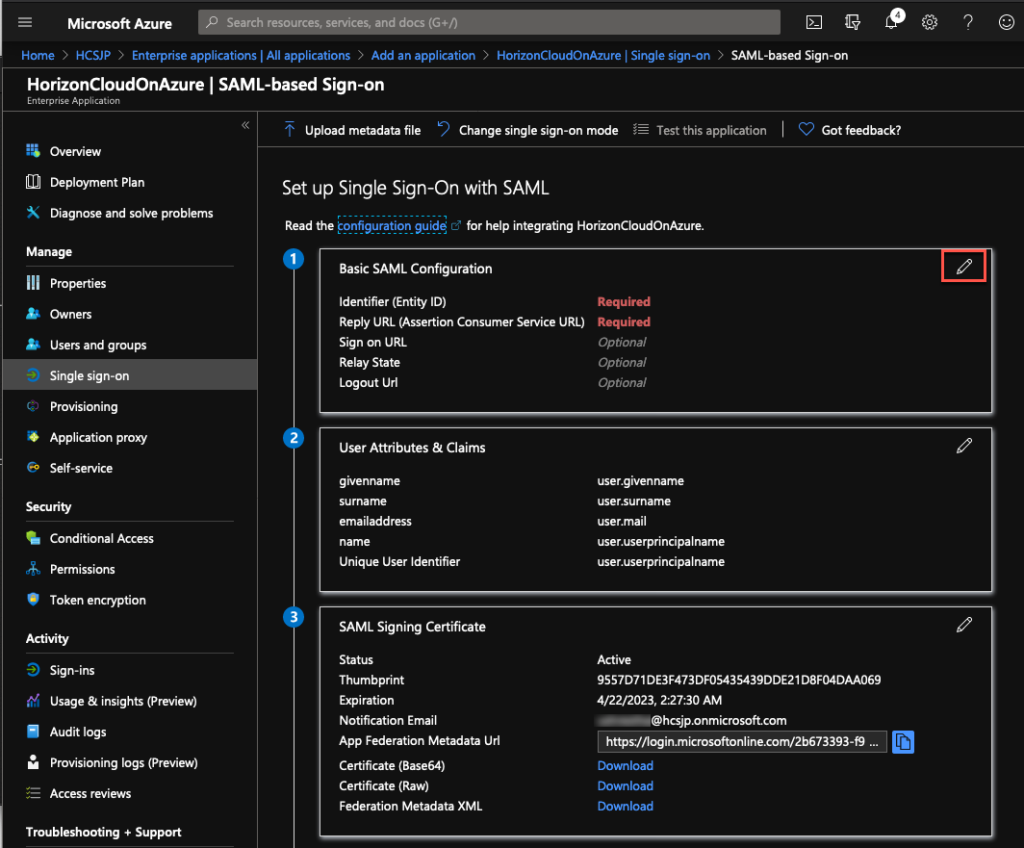
Note: To find the [Identifier] & [Reply URL] information, open below URL in your web browser.
https://[your tenant FQDN]/SAAS/API/1.0/GET/metadata/sp.xml

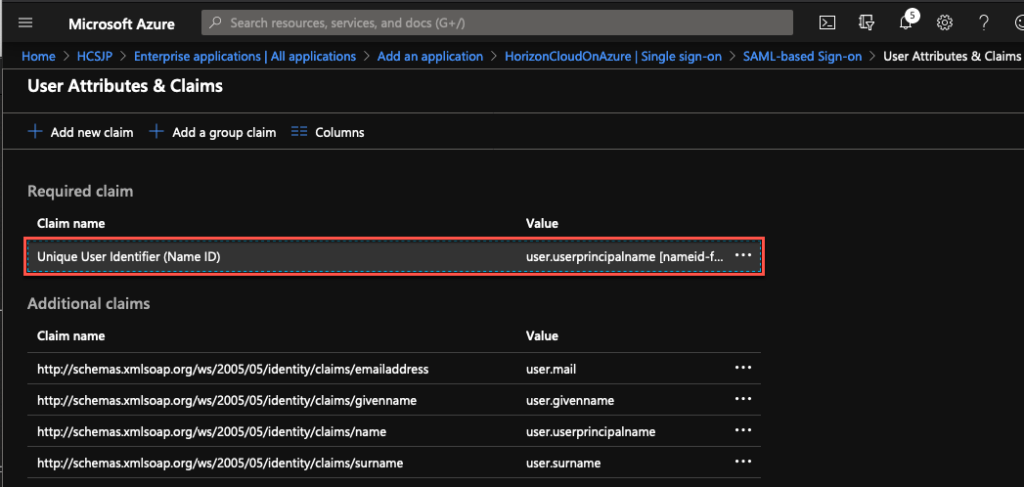
7. Double click on [Claim name] under [User Attributes and Claims].
8. Expand [Claim Conditions] and select [Any] under [User Type] dropdown.
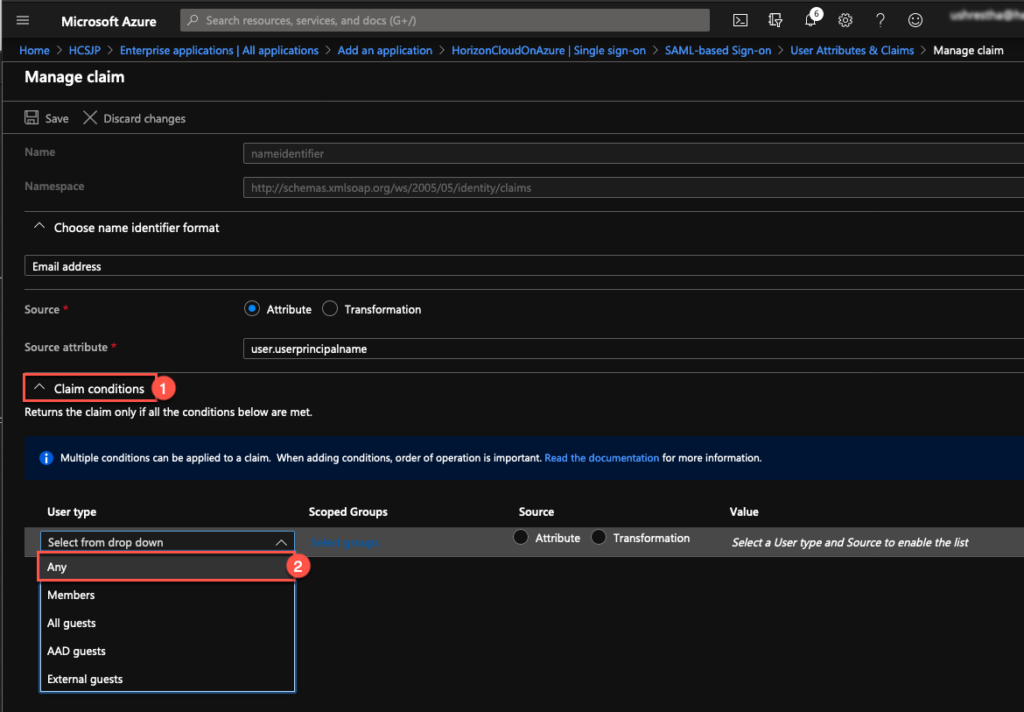
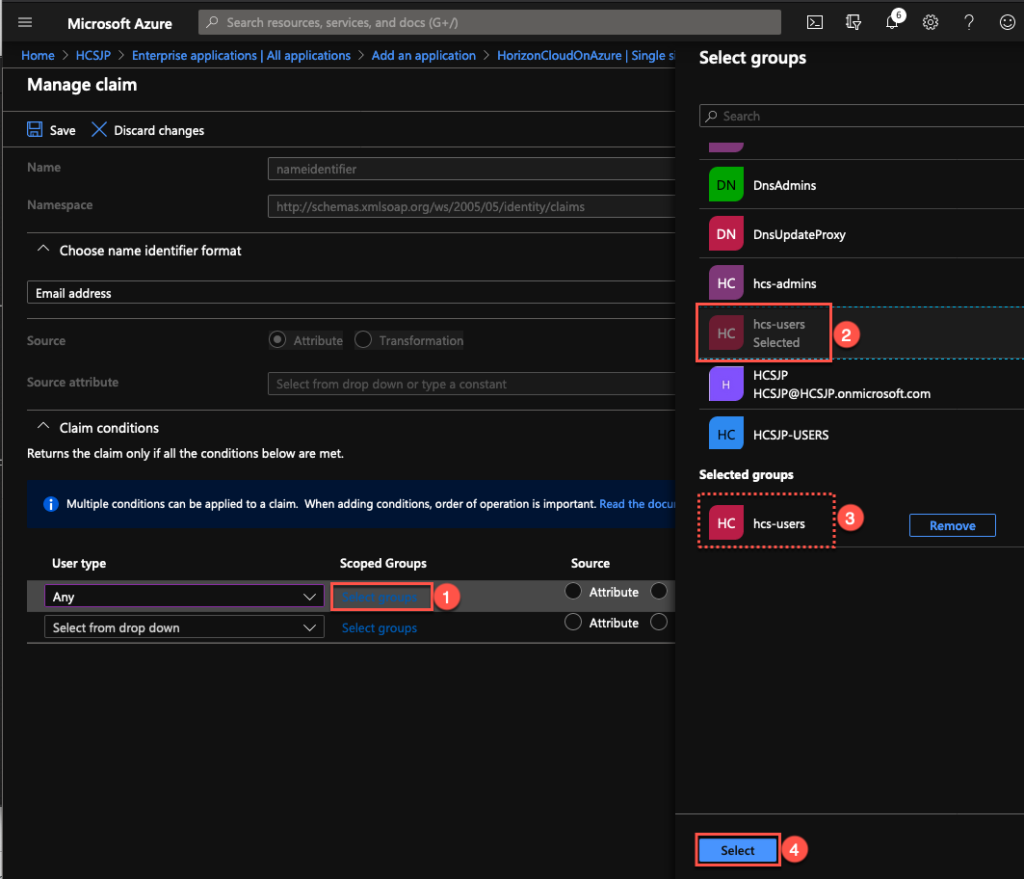
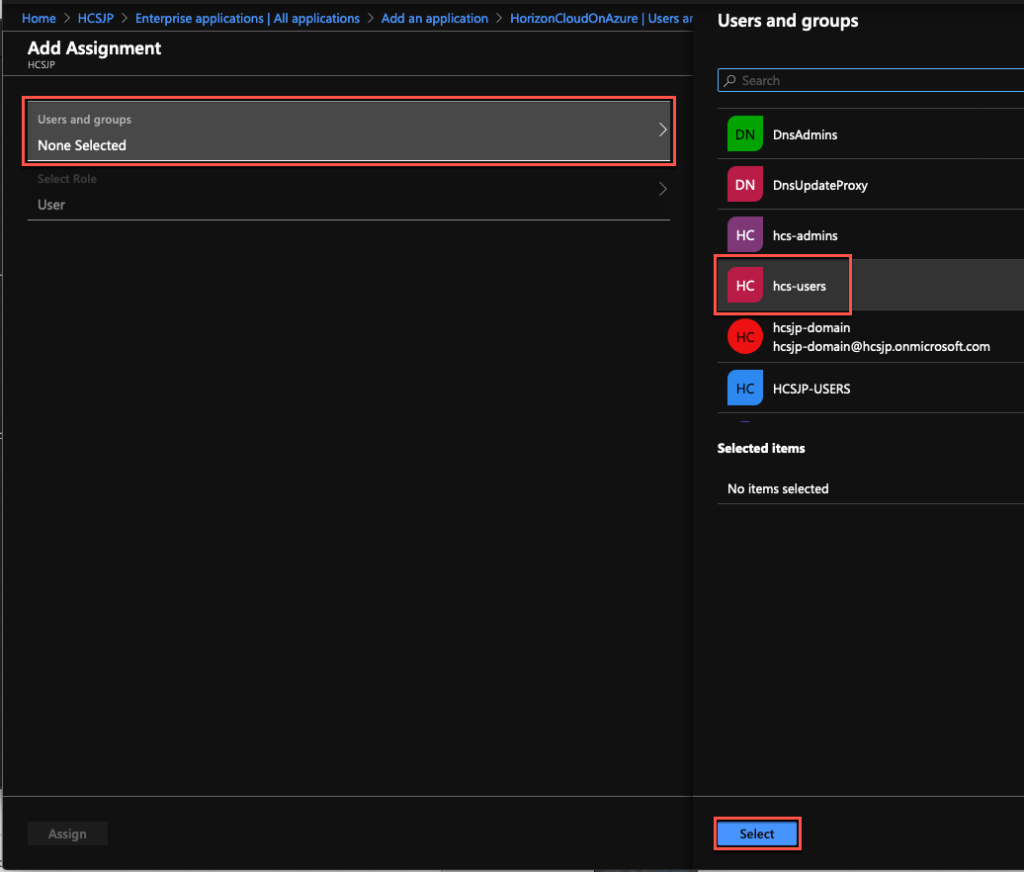
9. Double click on [Select groups] under [Scoped Group] column, select the AD users security groups which has HCS on Azure desktops/applications are entitled > [Select].
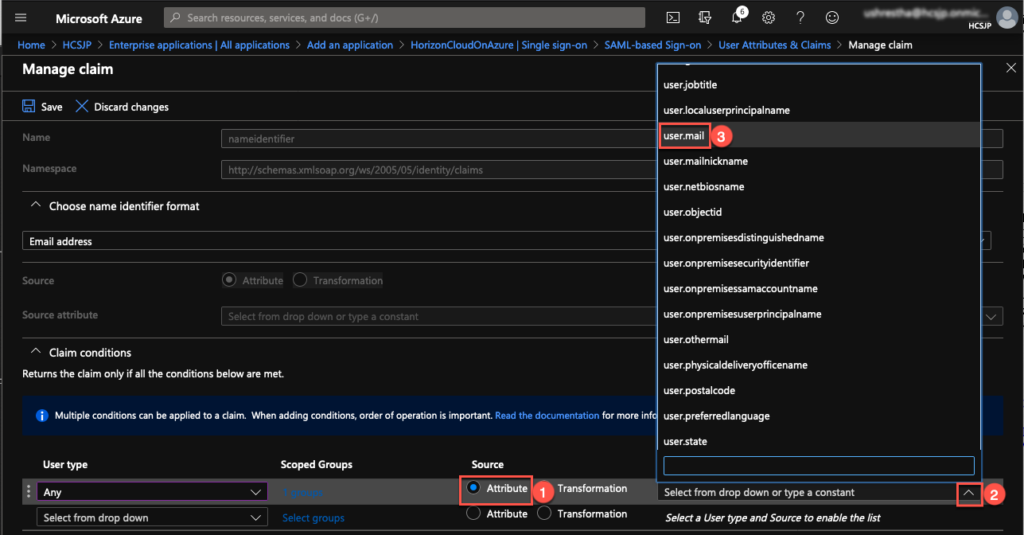
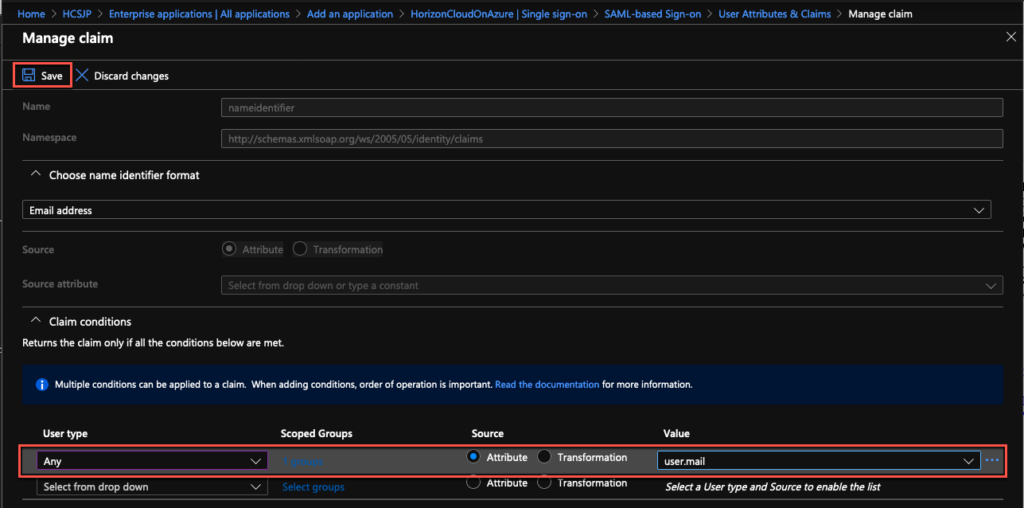
10. Select [Attribute] under [Source] column > select [user.mail] from dropdown > [Save].
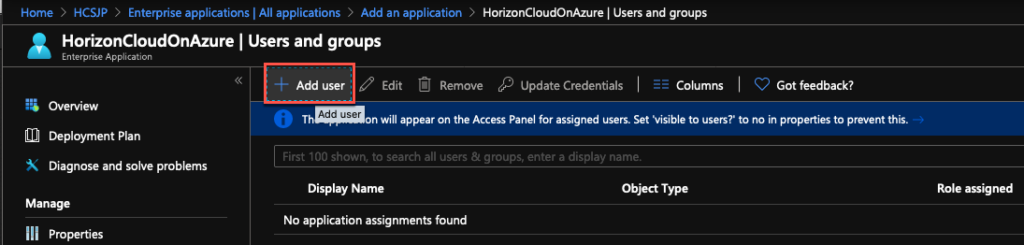
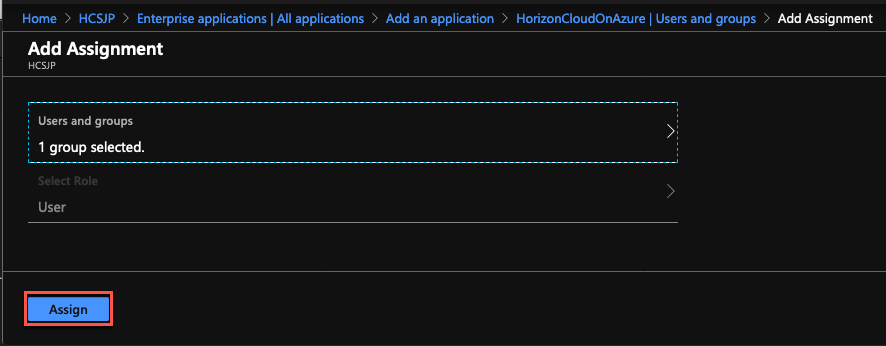
11. Select [Assign the users and groups] > [Add user] > choose the users/groups to which you need to allow the access to Enterprise application > [Select] > [Assign].
12. Next, you will need to configure Azure AD as 3rd party IDP in Workspace ONE Access admin console which needs Enterprise Application federation metadata XML file. Download the XML file from [Enterprise Application] > [Single sing-on] > [3. SAML Signing certificate].
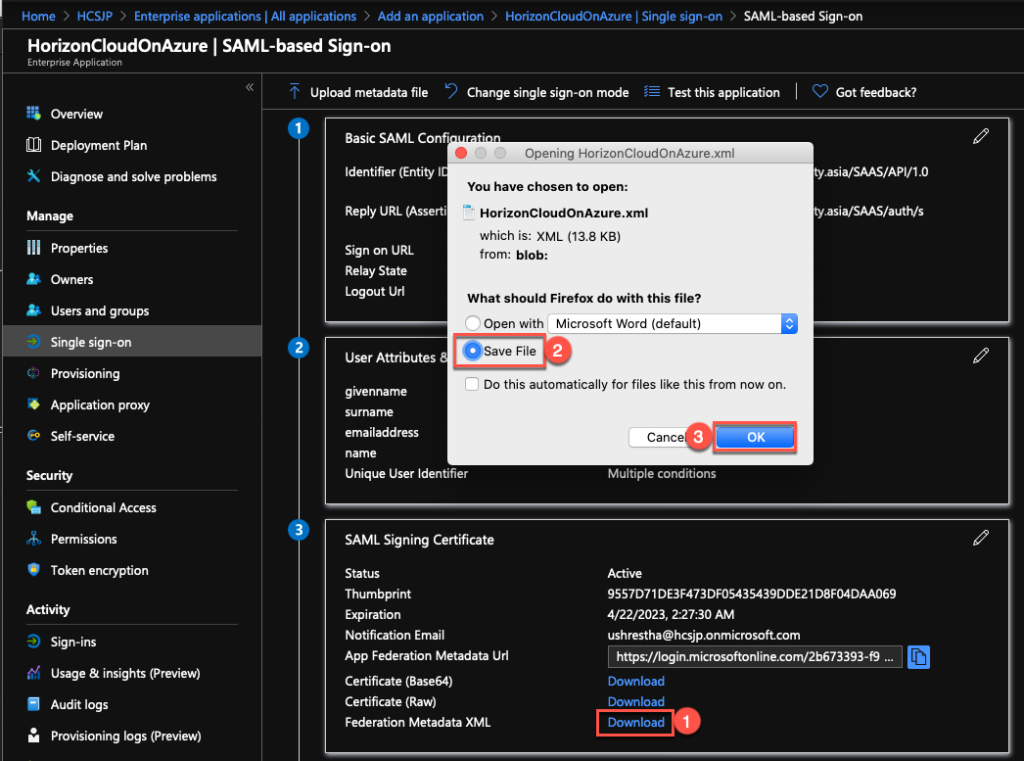
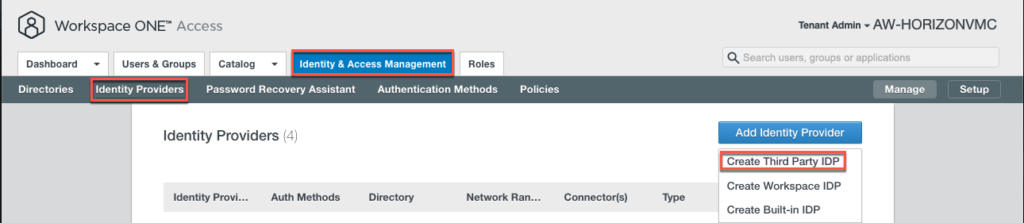
13. Login to VMware Workspace ONE Access admin console. Open https://[your tenant FQDN]/SAAS/login/0 in your web browser and select [Identity & Access Management] > [Identity Provider] > [Create Third Party IDP].
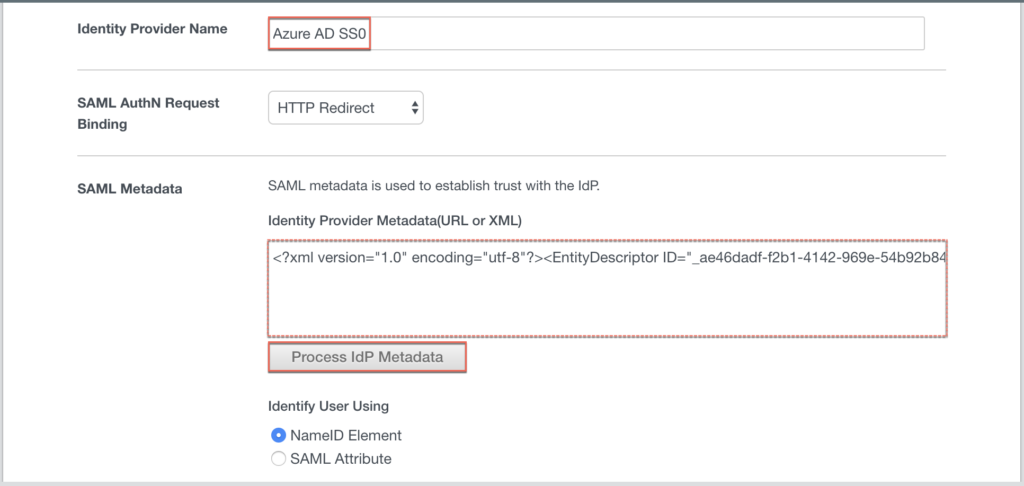
14. Give the name of your choice to Identity Provider which you are going to create > open the Enterprise Application Metadata XML file (downloaded in step-12) in text editor and paste all the contents into SAML Metadata field > [Process IdP Metadata].
Add the Name ID format mappings. In this case [email] and [userName].
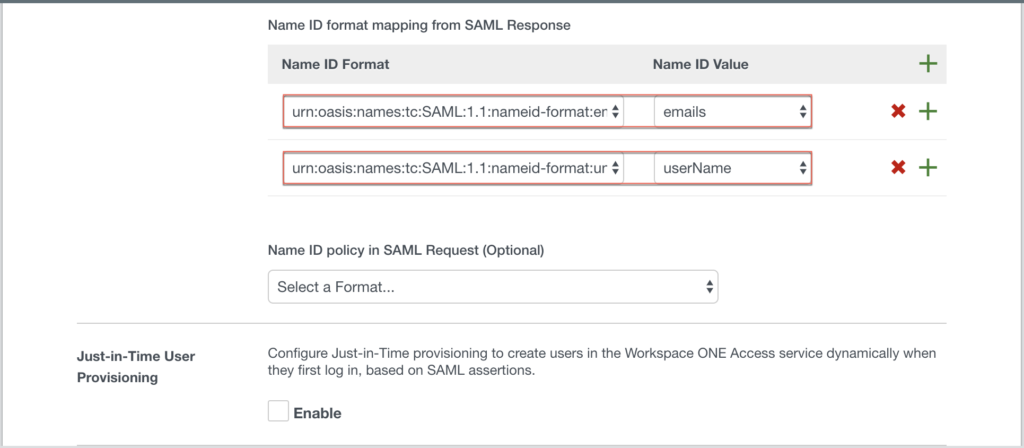
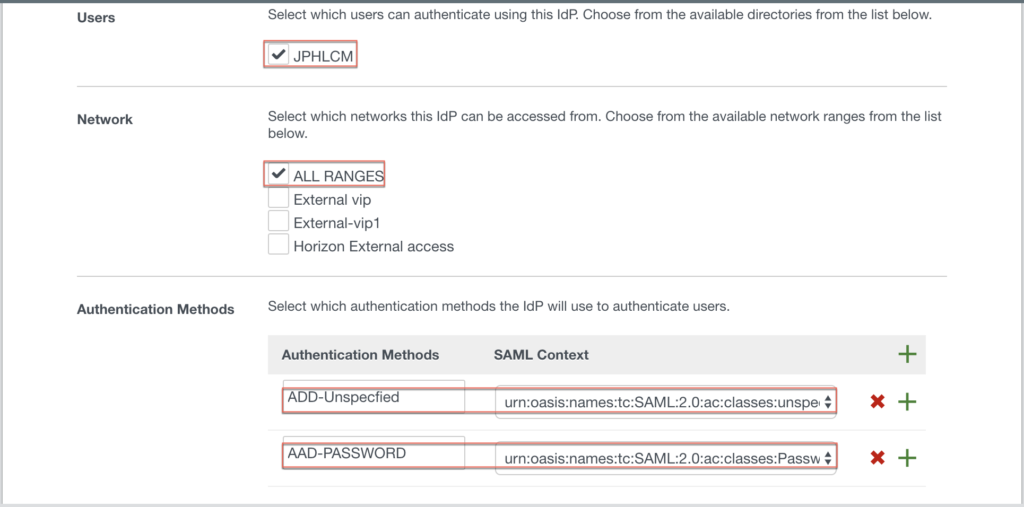
Select the directory that you have already added to your Workspace ONE Access tenant. In this case directory as [JPHLCM], Network as [ALL RANGES] and add [Authentication Methods] as below.
- urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified
- urn:oasis:names:tc:SAML:2.0:ac:classes:Password
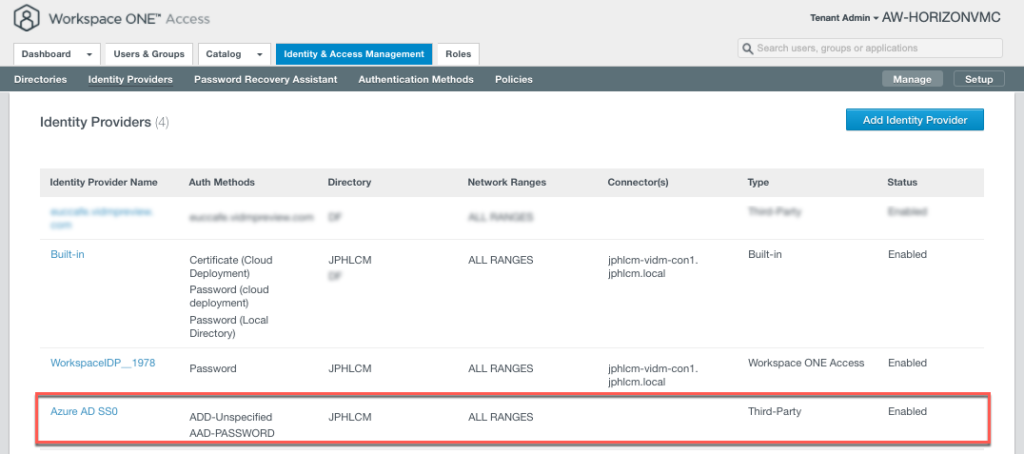
16. Confirm the Identity Provider has been added successfully and state is showing as [Enabled].
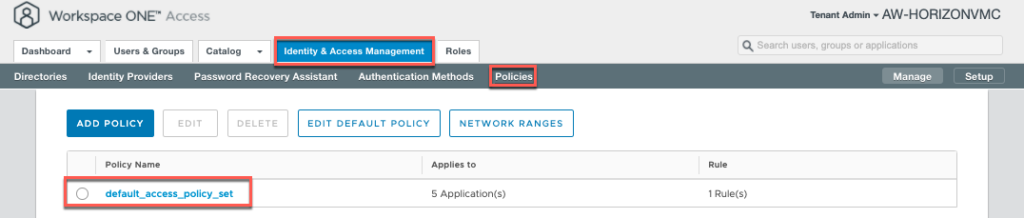
17. Next we need to configure the access policy allowing Azure AD Authentication Methods (configured in step-15) to authenticate the applications (HCS on Azure desktops in this case). Select [Identity & Access Management] > [Polices] > [default_access_policy_set] > Edit.
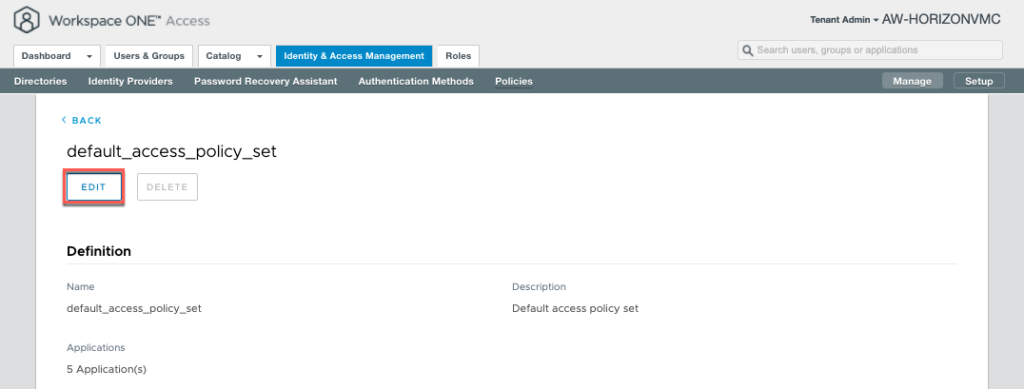
18. Configure the parameters as below and [Save].
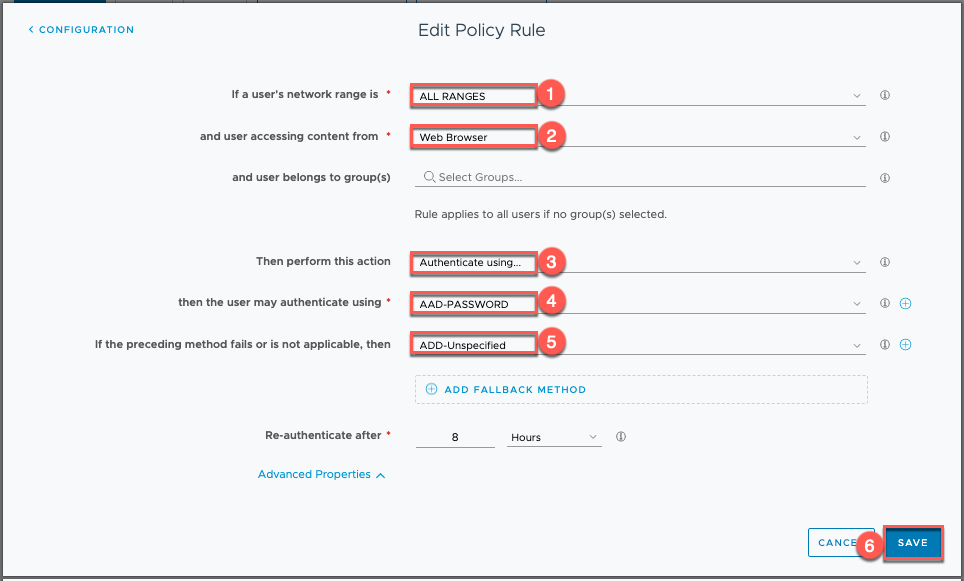
19. We are now all set with the configuration. Before moving forward to login test, let’s double check if the points below has been done.
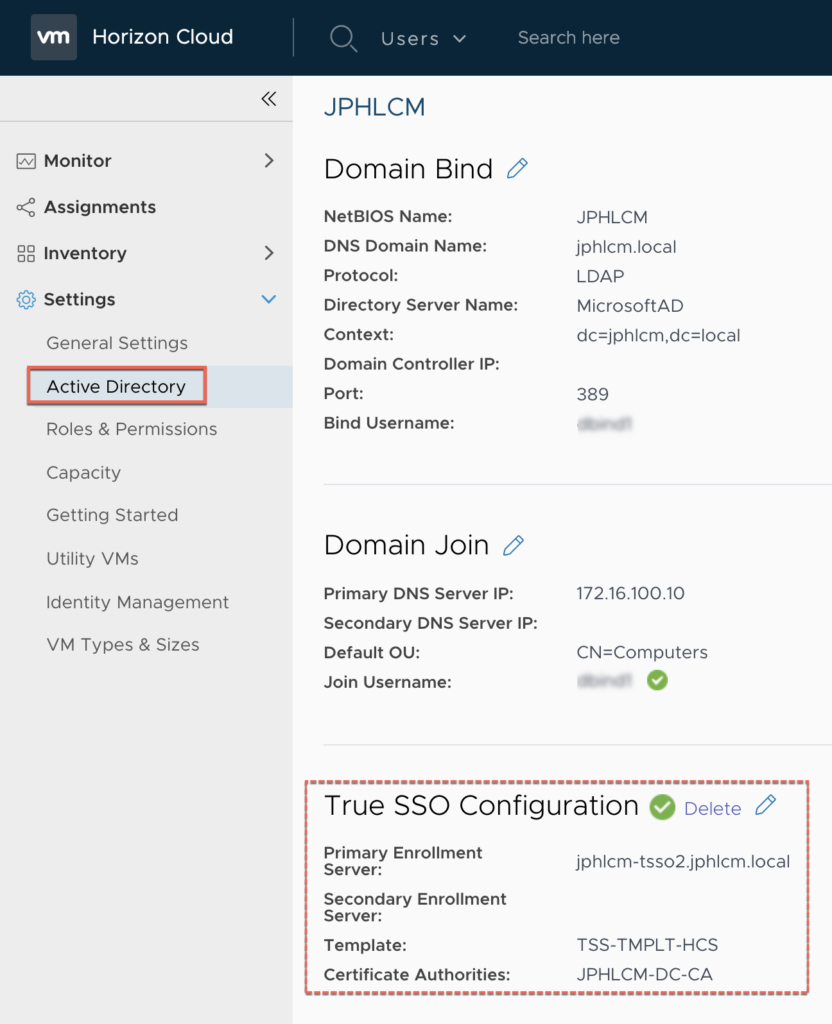
- Confirm True SSO feature in HCS on Azure admin console is configured and is in active state. [Settings] > [Active Directory] > [True SSO Configuration].
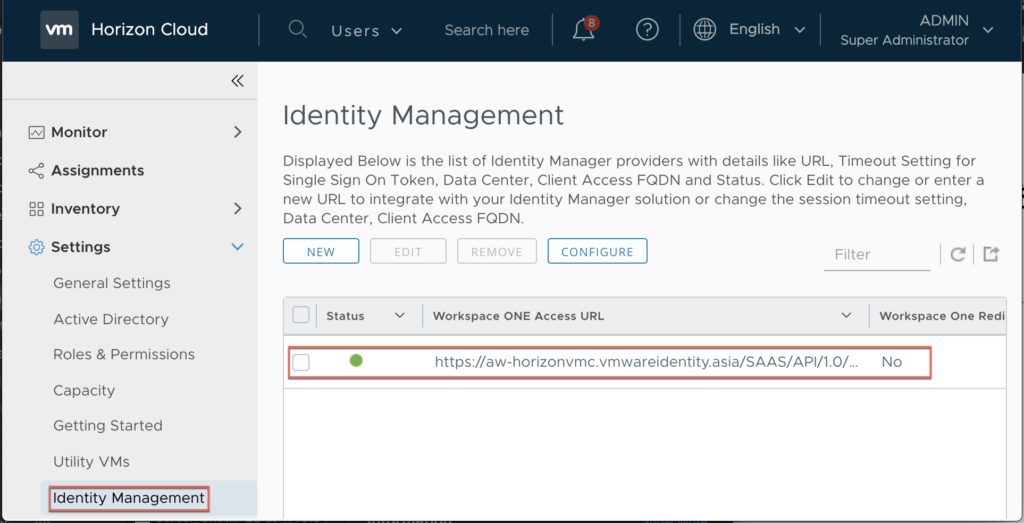
- Confirm Workspace ONE Access tenant is registered in HCS on Azure POD. [Settings] > [Identity Management].
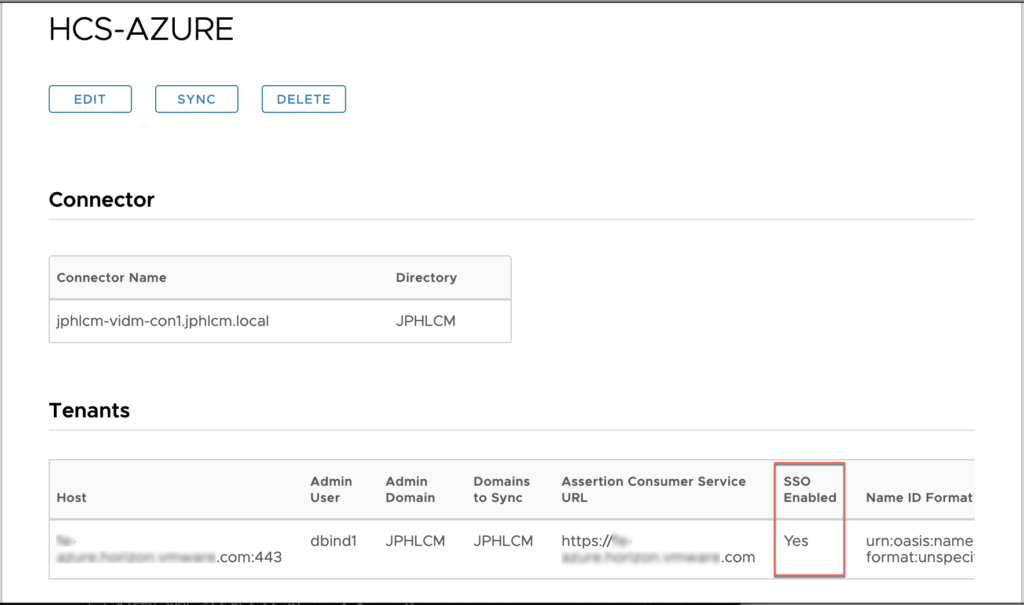
- Confirm True SSO feature is enabled in Workspace ONE Access admin console. [Catalog] > [Virtual Apps Collection] > [HorizonCloud App].
20. Now let’s confirm if user is able to login to HCS on Azure desktops with Azure AD single sign-on.
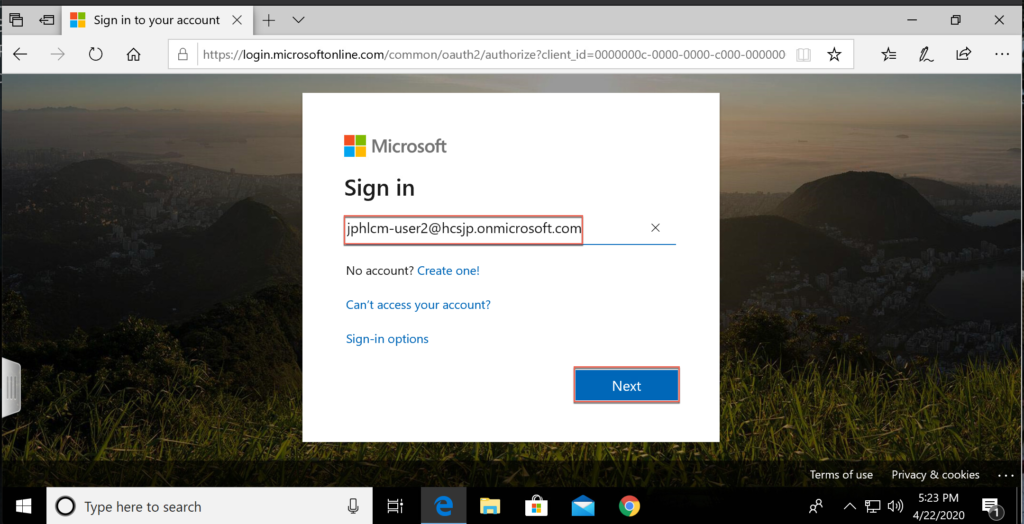
- Access https://myapps.microsoft.com in web browser and login with Azure AD user/password.
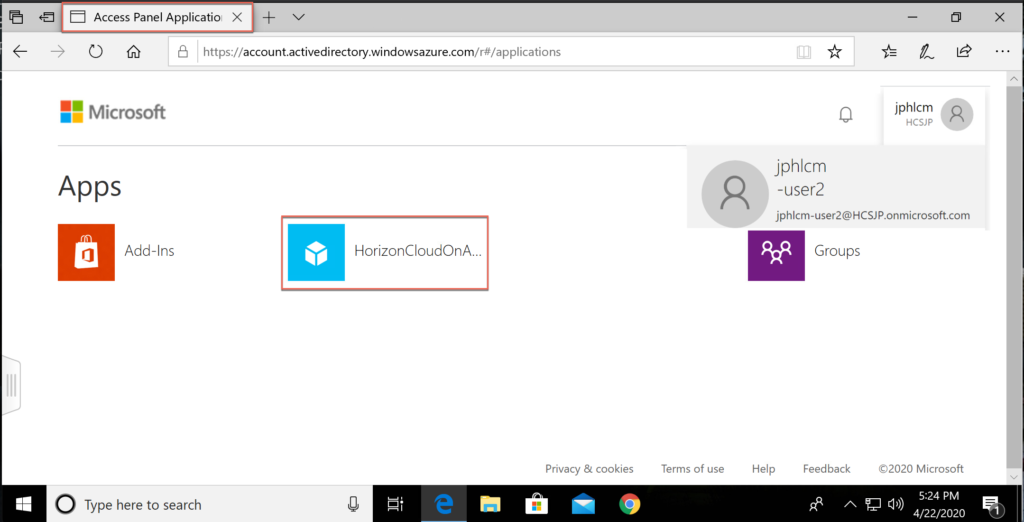
- Open application [HorizonCloudOnAzure].
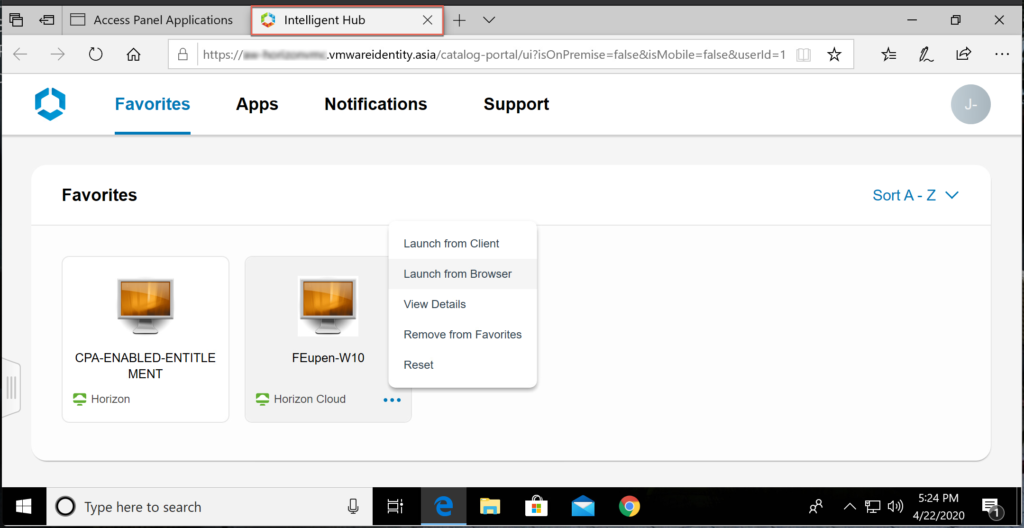
- Lunch the Horizon Cloud desktop
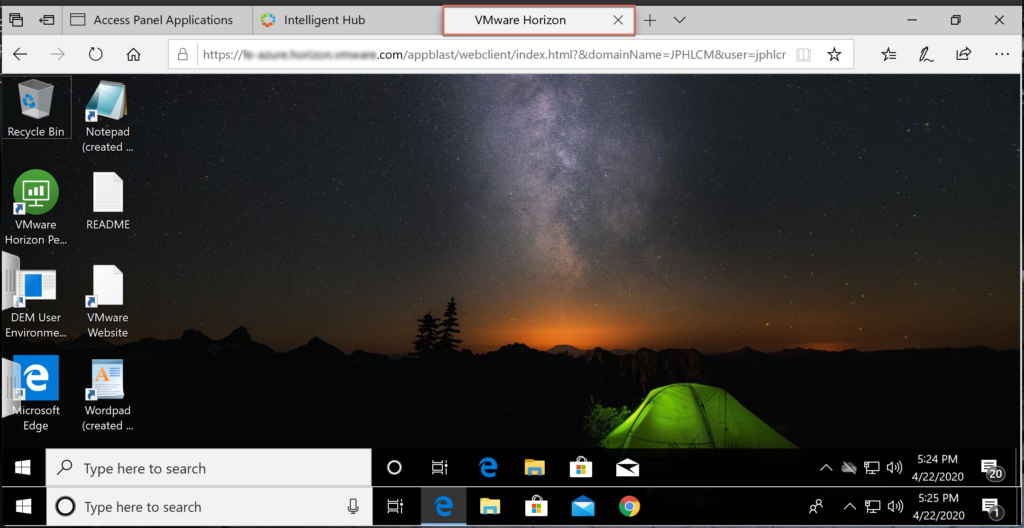
- If everything is configured properly, you should be able to get the desktop.
At the end, let’s see the video which shows how the user logs into VMware Workspace ONE Access using Azure Active Directory as 3rd party IDP and how trueSSO feature works in HCS on Azure.